User Management
Introduction
The User Management section allows administrators to create, edit, and manage user accounts for your Aether CMS installation. This powerful feature helps you control access to your site's administration area and assign appropriate roles to team members.
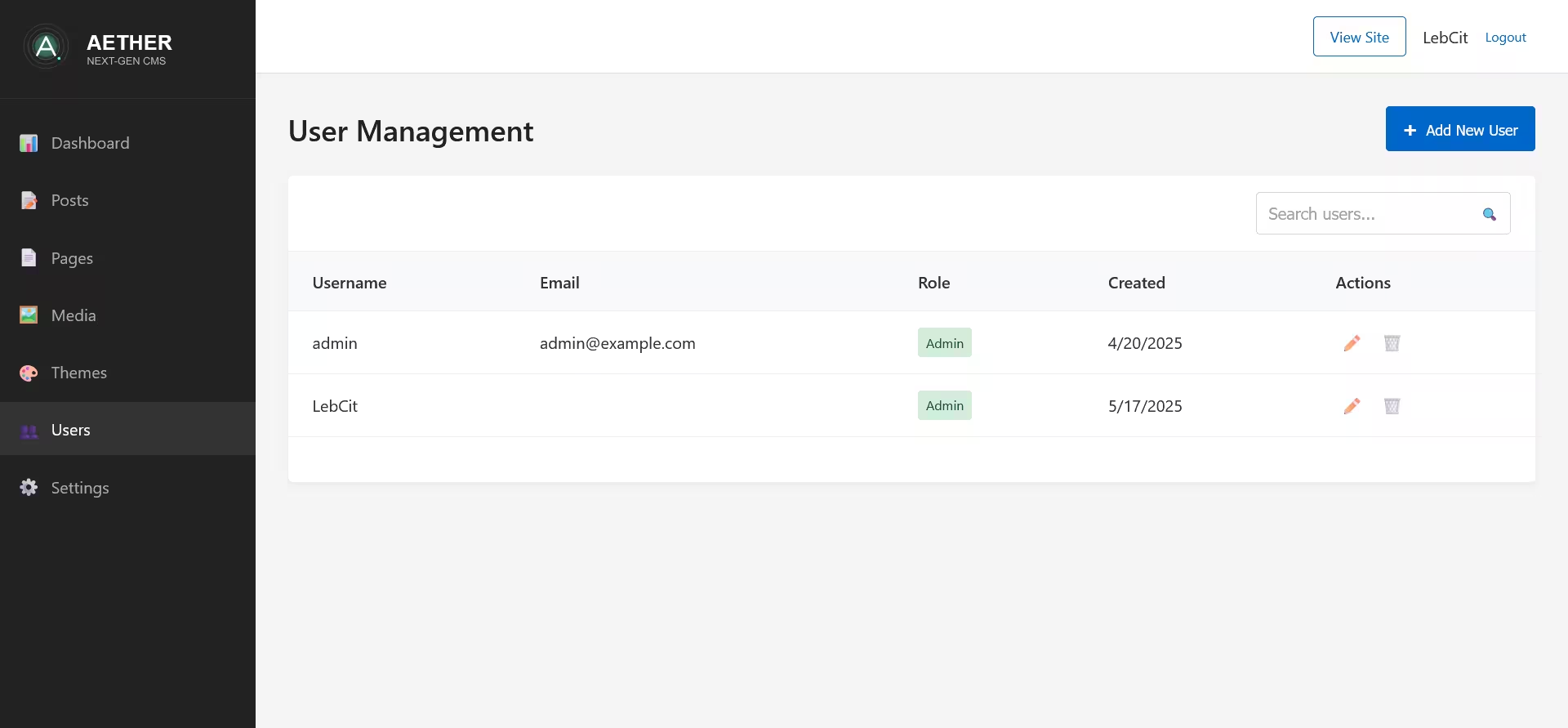
Accessing User Management
To access the User Management page, click on "Users" in the sidebar navigation. Note that only administrators have access to this section.
Interface Overview
The User Management interface consists of several key components:
- Header Bar: Contains the title and "Add New User" button
- User Creation/Edit Panel: Form for adding or modifying users
- User Search: For finding specific users
- Users Table: Displays all user accounts in a tabular format
User Roles
Aether CMS supports two main user roles:
- Administrator: Full access to all features, including user management
- Editor: Can create and manage content, but cannot access user management or generate a static site
Managing Users
Viewing Users
The Users Table displays all user accounts with the following information:
- Username
- Role (Administrator or Editor)
- Creation date
- Action buttons (Edit and Delete)
You can search for specific users using the search box in the top right corner, which filters the table based on username, email, or role.
Adding a New User
To add a new user to your site:
- Click the Add New User button in the top right corner
- The user creation panel will appear with the following fields:
- Username (required)
- Email (required)
- Password (required for new users)
- Role selection (Administrator or Editor)
- Fill in the user information
- Click Save User to create the account
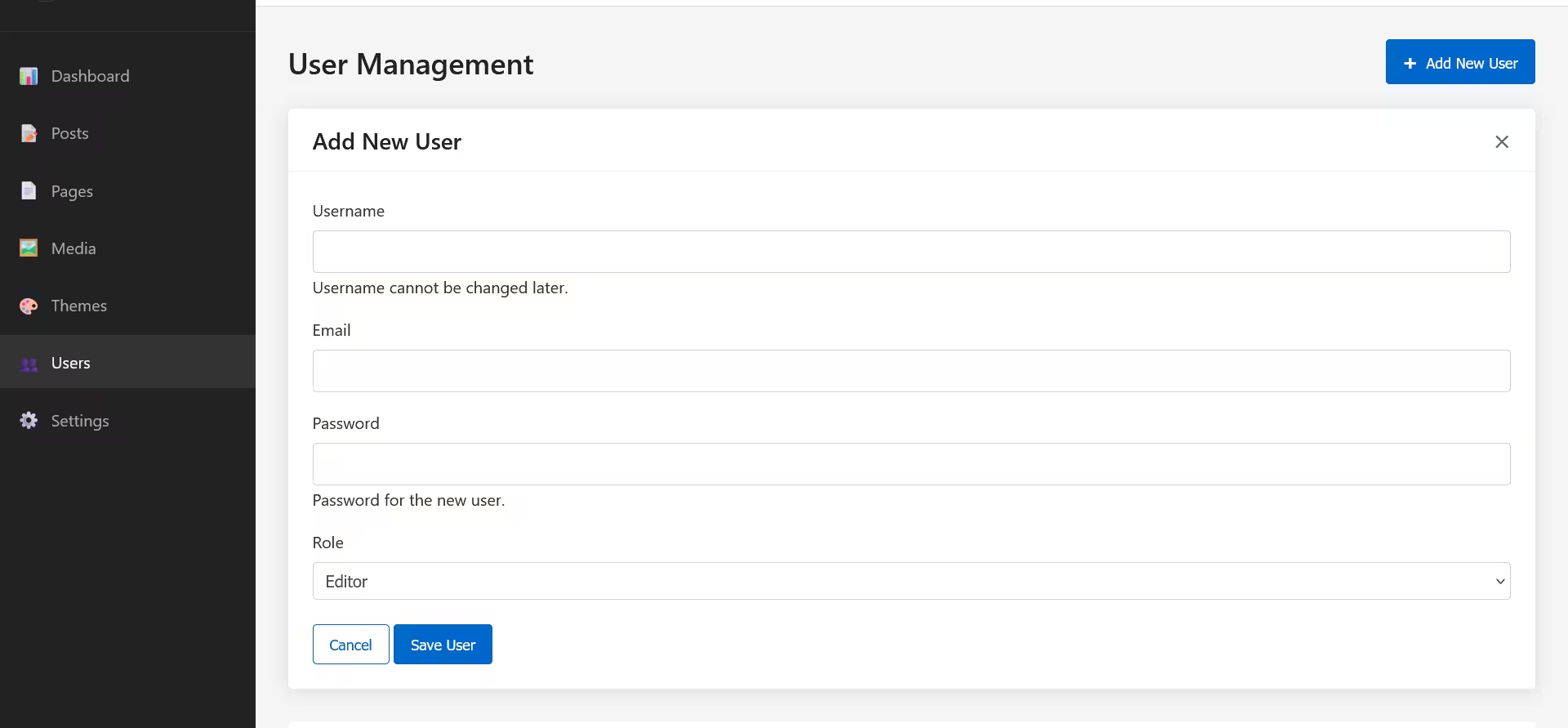
Username requirements:
- Must be unique
- Cannot be changed after creation
- Should contain only letters, numbers, underscores, and hyphens
Password guidelines:
- Should be secure and complex
- No requirements enforced by the system
- Responsible for communicating the password to the new user
Editing Users
To edit an existing user:
- Click the Edit button (pencil icon) next to the user in the table
- The user edit panel will appear with pre-filled information
- Make your changes to the email or role
- Optionally enter a new password (leave blank to keep the current password)
- Click Save User to update the account
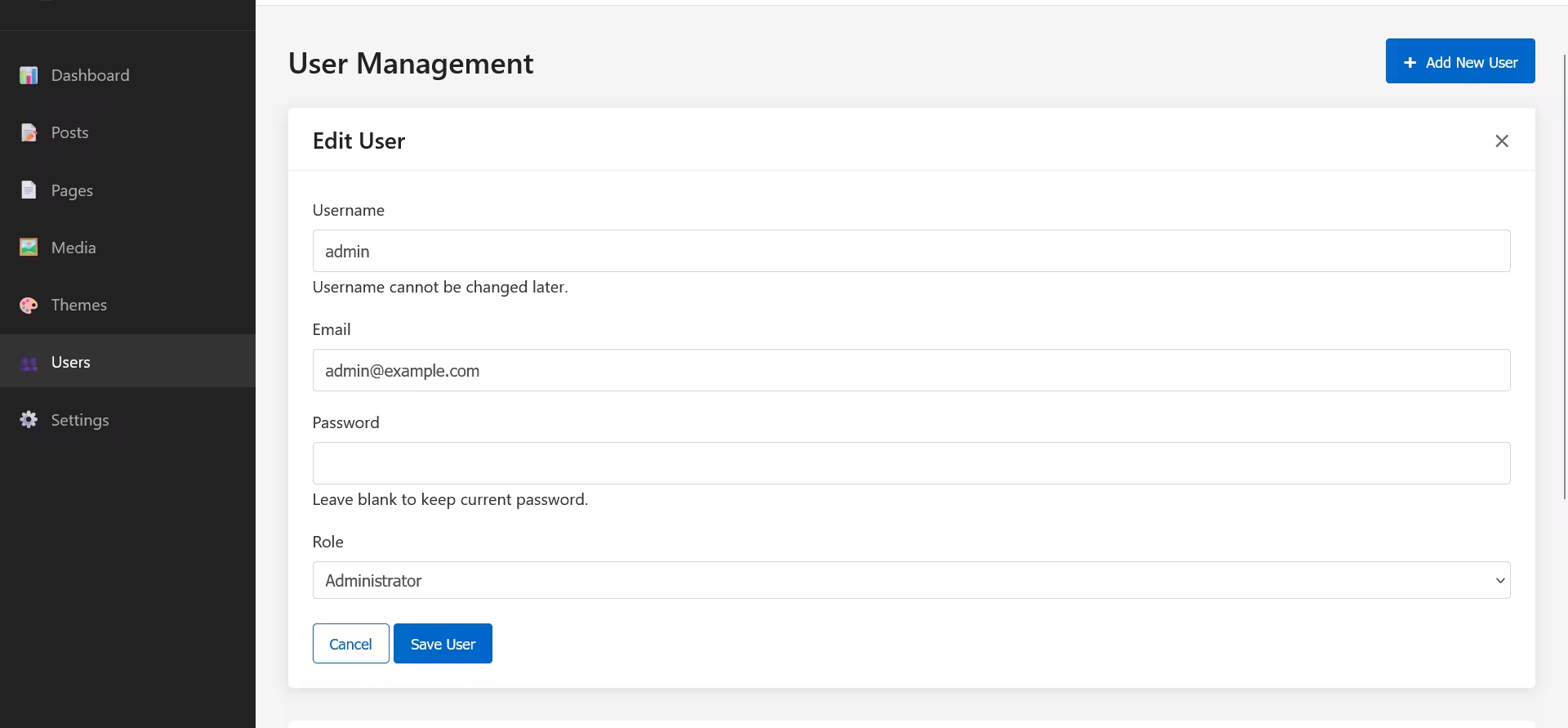 When editing a user:
When editing a user:
- Username cannot be changed
- Password field is optional (leave blank to retain the current password)
- Email and role can be modified
Deleting Users
To delete a user account:
- Click the Delete button (trash icon) next to the user in the table
- A confirmation dialog will appear
- Click Delete to confirm the deletion
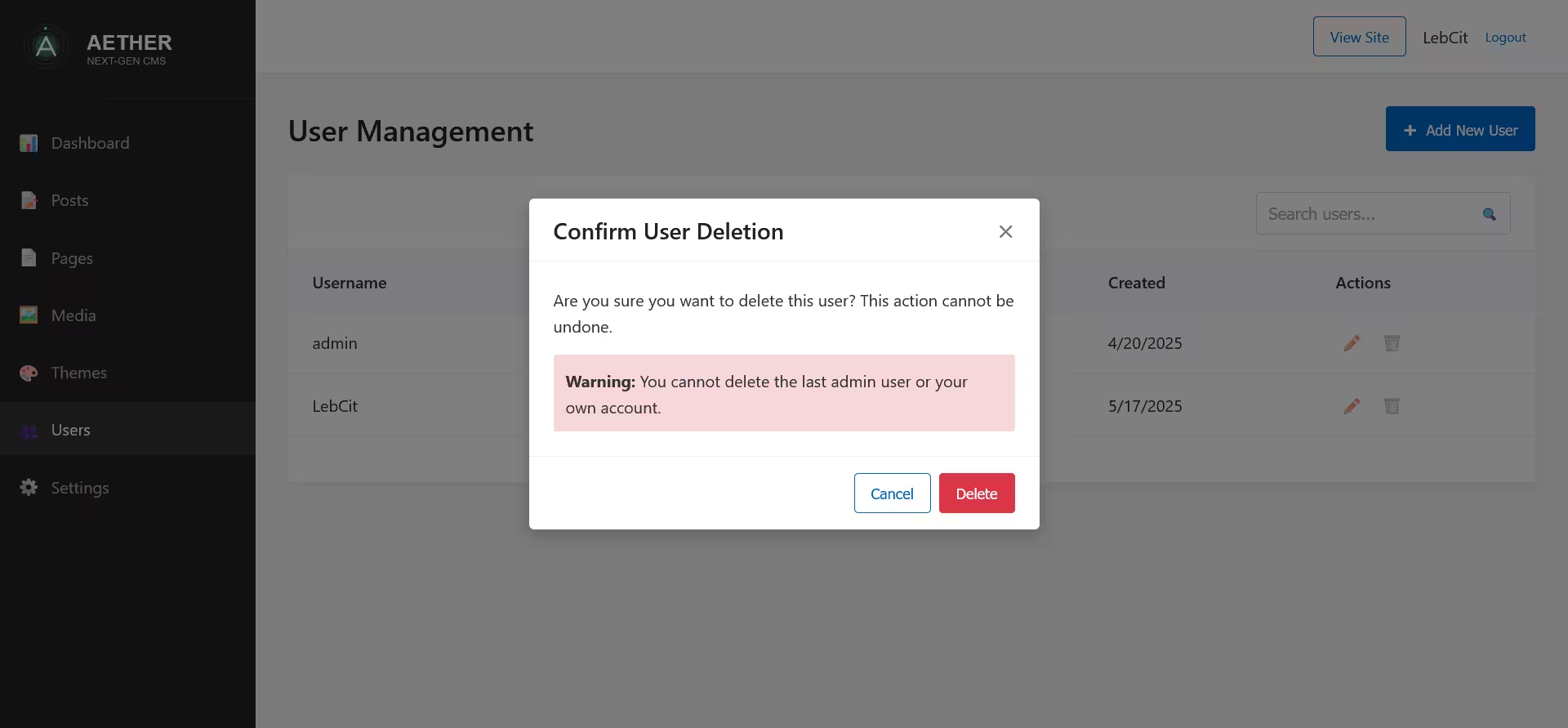
Important deletion limitations:
- You cannot delete your own account
- You cannot delete the last administrator account
- The system will display a warning if either of these conditions is met
Security Considerations
The User Management system includes several security features:
Password Handling
- Passwords are securely hashed before storage
- Password fields are never pre-filled when editing users
- Original passwords cannot be recovered (only reset)
Role Permissions
- Only administrators can access the User Management section
- Editors cannot modify other user accounts
- Role-based access control throughout the system
Responsive Behavior
The User Management interface is fully responsive:
- Desktop: Displays the full user table with all columns
- Tablet: Hides less important columns (creation date)
- Mobile: Further simplifies the display for smaller screens
Best Practices for User Management
- Limit administrator accounts to only those who need full system access
- Use unique, strong passwords for each user account
- Regularly audit user accounts to ensure they are still needed
- Assign appropriate roles based on the principle of least privilege
- Create dedicated accounts for each team member rather than sharing credentials
